What is HIPAA?
HIPAA (Health Insurance Portability and Accountability Act) is a U.S. federal law that protects patients’ sensitive health information from being disclosed without their consent or knowledge.
These rules apply to all entities, known as “Covered Entities”, that collect, store, transmit, or use PHI. These Covered Entities are required to ensure the confidentiality, availability, and security of PHI and must abide by the Privacy Rule’s regulations regarding the use and disclosure of PHI.
This includes implementing safeguards to protect PHI’s privacy in CRM and restricting its use and disclosure only to authorized purposes.
The Privacy Rule also grants individuals the right to access and control their PHI, including the right to request a copy of their PHI, to have errors corrected in their PHI, and to be notified of any unauthorized use or disclosure of their PHI.
Who must follow HIPAA?
1. Health care providers
As long as they exchange data, “health care provider” refers to nearly all parties involved in the medical practices:
- Doctors
- Clinics
- Psychologists
- Physicians chiropractors
- Chiropractors
- Nursing homes
- Pharmacies
2. Health plans
It includes health insurance companies, HMOs, company health plans and government programs that pay for healthcare (Medicare, Medicaid).
3. Health care clearinghouses
Health care clearinghouses process nonstandard health information they receive from another entity into a standard format.
4. Business associates
Third parties that perform services for a covered entity and use or disclose protected health information are considered business associates. This includes entities based overseas, such as management services and data processors (CRM platform).
HIPAA states that all personally identifiable health information held or transmitted by a covered entity, regardless of how it is collected, shared, transmitted, or stored, is subject to the Privacy Act’s requirements.
Protected Health Information (PHI)
According to HIPAA rules, HIPAA applies to all 18 fields of “personally identifiable health information” owned or disclosed by a Covered Entity or its Business Associate, whether electronic, paper, or oral.
- Name
- Address
- Date of birth
- Social Security Number
- Medical history
- Photographs
Names, addresses, and phone numbers do not constitute PHI, unless you link them to medical details, healthcare services or treatments.
When sending appointment reminders, for example, it’s best to avoid including specific details. Simply write something like “I remind you of your appointment on [date] at [location]”. No need to mention the treatment or specialty.
Most Common HIPAA Violations
The most common HIPAA violations are those committed internally, usually due to a lack of diligence in following the guidelines of the rule.
Organizations can break the rules by not keeping patient information safe, not training employees on how to protect confidential data, and not disposing of sensitive records correctly.
Other violations include not providing the necessary notices to patients regarding their health information, not adhering to the proper processes for requesting and granting access to medical records, and not properly monitoring and auditing employee access to confidential data.
Even seemingly minor infractions can lead to serious consequences, such as hefty fines and potential jail time.
Common violations include:
- Publishing PHI online
- Sending PHI in error
- Office break-in
- Cyberattack
HIPAA Technical Safeguards
Technical safeguards are “the technology and the policy and procedures for its use that protect electronic protected health information and control access to it”.
A covered entity must implement security measures that are reasonable and appropriate for their organization in order to maintain the necessary standards for protection.
These measures must be reasonable and appropriate for their organization, taking into account the size, complexity, and scope of their operations, as well as the potential risks to the protected health information they are responsible for protecting.
Measures include administrative, physical, and technical safeguards to ensure the confidentiality, integrity, and availability of the information.
Additionally, they should have a process in place to regularly review their security measures and update them as needed to ensure that they remain adequate and effective.
Access control
Access controls should be in place to ensure that only those who need access to PHI are able to access it. Access controls should enable authorized users to access only the minimum necessary information needed to perform their job functions.
Integrity
In addition, as a covered entity you must implement policies and procedures to shield PHI from improper modification or destruction.
Organizations can also determine how outside sources could alter information integrity. Audit logs and secure backups will help maintain data integrity.
Secure data transmission
Healthcare organizations are also dependent on secure data exchanges (data security), particularly because of the rise of electronic health records and health information exchanges (HIEs).
Transmitting PHI via email
HHS considers consent implied if an individual provides a healthcare provider with an email address or initiates communication through email. Nevertheless, you should warn about the potential risks of sharing PHI via email and document this information.
In accordance with HHS guidance on HIPAA email requirements, it is essential to implement reasonable safeguards for the transmission of PHI through email, adhere to the minimum necessary standard, and ensure that the electronic transmission of PHI complies with the Security Rule.
Despite these guidelines, sending PHI via email is strongly discouraged. We recommend alternative methods, such as password-protected storage accessible only through secure (https) connections.
A practical solution for sending confidential information via email is Secret Once (secretonce.com), which is free to use but also allows file transfers in the business version.
CRM to improve the patient experience
Providing great medical care can be both easy and complex depending on the situation. For some healthcare professionals, providing quality care may be relatively straightforward.
However, for others, providing great medical care can be a time-consuming and tedious process. Diagnosing and treating patients can involve carefully examining symptoms and medical history, ordering and interpreting test results, and exploring different treatments and medications.
Additionally, medical professionals must also take into account their patient’s lifestyle, cultural background, and personal preferences when creating an effective treatment plan.
Many workers dread the routine tasks that come with the job, such as scheduling appointments, making referrals, and updating patients about test results. These tasks can take away from providing a high-quality patient experience.
These challenges were exactly what CRM – Customer Relationship Management CRM Software – was supposed to solve.
Sales teams in the healthcare industry can use CRM software to improve operations and patient retention.
Organizations that want to link their CRM account to EHR can use API and Widgets from our CRM portal to enable integrations with other applications and content personalization.
With our API, you can sync your CRM data with external applications and databases in real time.
This way, you can have all the information you need within Onpipeline, such as hospital information, billing details, or any relevant data during the sales process.
Our API is easy to use for even mid-level developers. If you need any technical support or information, our team is available to help.
What is a Business Associate Agreement?
HHS says that anyone who does things that need access to PHI for a covered entity is considered a Business Associate.
This individual or organization may also provide services to a covered entity. Examples of services include reviews, legal services, Cloud Service Providers (CSPs) and HIPAA compliant CRMs .
HIPAA authorizes covered entities to disclose protected health information only to assist the covered entity in its health-care activities.
A business associate agreement (BAA) is used to establish the responsibilities of a business associate in regards to safeguarding a patient’s PHI (HIPAA compliance). This agreement outlines the expectations and requirements of both parties, and is legally binding.
What is a Healthcare CRM Solution?
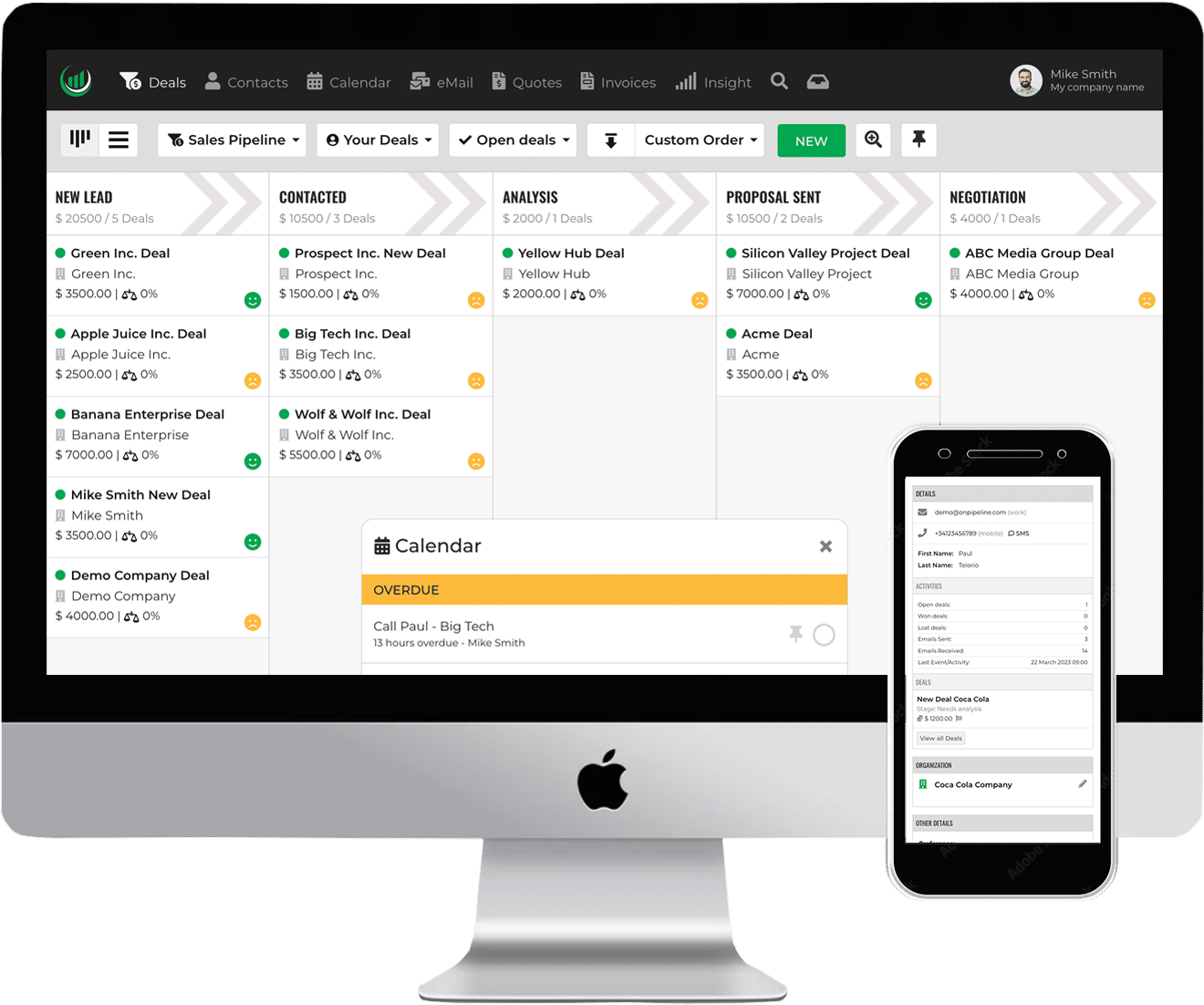
It is a system for managing patient acquisition, patient relationships, patient information, interactions, and spending. You can update details for all your patients within a single platform and obtain a complete real time view.
With our easy to use CRM, your healthcare organization has the option to add custom fields to best fit your individual needs.
You can obtain a variety of views to deliver personalized experiences, allowing you to access patient demographics, patient data, activities, conversations, phone calls, emails, and much more.
With Onpipeline, you can monitor your patient’s journey from the initial contact to full resolution of their needs, providing better care and more efficient operations.
Is Onpipeline HIPAA compliant?
Onpipeline CRM is a HIPAA compliant CRM Software. We meet the physical and technical safeguards as required by HIPAA.
We encrypt data stored on our servers. Data transmission is done via HTTPS / Secure Sockets Layer where we obtain A+ overall rating (which is the maximum).
Two-factor authentication (2FA)
Prevent unauthorized access to user accounts, even in the event of a compromised password. By implementing 2FA, an additional layer of security is introduced. This involves generating a unique, one-time verification code that is delivered to the user’s email inbox each time they attempt to login with their identification and password credentials.
IP Restriction
Define particular IP addresses to permit account access is a useful tool to restrict entry only to users located in a specific area (such as the office or a VPN). Any user attempting to log in with an IP address that is not recognized and included within the specified list will receive an error message and be barred from progressing any further.